On August 12th, ShadowMap A cyber-threat intelligence platform has published a post which was later unpublished, on how they were able to access AarogyaSetu's original source code. Even though it is popular belief that the source code of AarogyaSetu is already public, it was only a limited part of the code & not the original code repository which the team was using for active development. The github page of public code was not updated since 29th May 2020. ShadowMap found out one of the developers of the AarogyaSetu has left the original github url and its access credentials in plain-text in a public webroot folder.
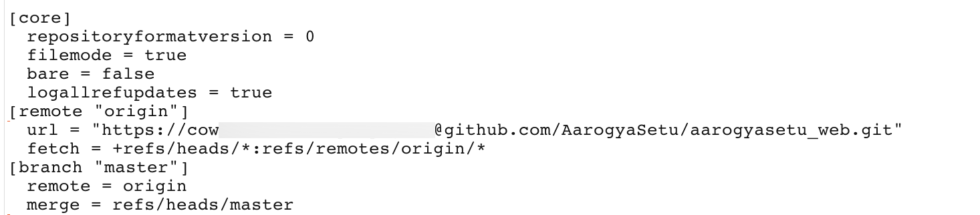
The ShadowMap team bypassed two factor credentials using GitHub API and directly accessed the entire code repository. They were able to access 10 repositories and were able to download the source code for the Aarogya Setu website, Swaraksha portal, back-end APIs, web-services, internal analytics / correlation code, SQS Handler, OTP Service, etc.
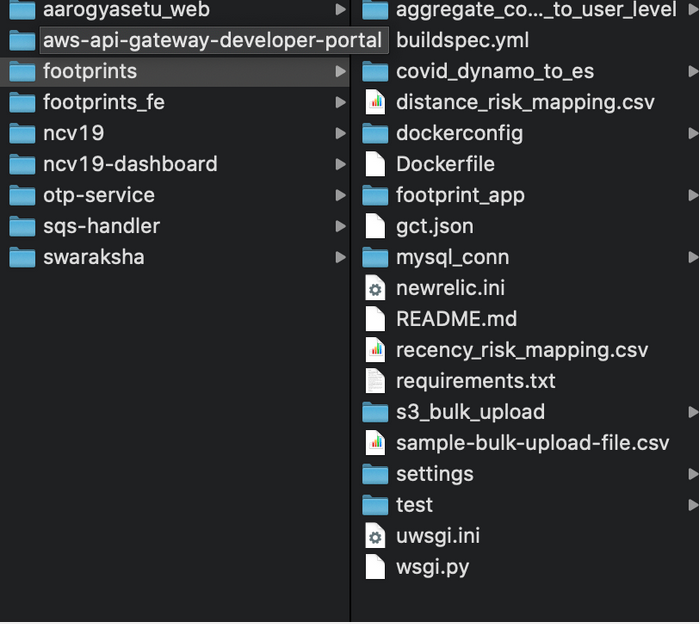
According to ShadowMap, they reported the issue to NIC, NIC CERT & Aarogya Setu team. However, they received no acknowledgement and the issue was silently fixed the next day. They were also able to access the source code of the KaiOS app from Openforge website, which is Government of India's code repository platform. Government of India has announced a bug bounty program for Aarogya Setu and ShadowMap technically deserves a bounty for reporting this to the authorities, instead they didn't even receive an acknowledgement.

The ShadowMap team has not made the source code public, but has pointed out their analysis. With AarogyaSetu app being developed by private volunteers, private infrastructure was also used for development of the app. They were able to find out the app using infrastructure from GoIbibo Group. They pointed out the line between private players and AarogyaSetu team is very thin and there was no layer to differentiate. With the security practices and access to private firms and individuals, ShadowMap raised concerns over accountability and expertise of these private volunteers. Considering they don't have any contractual or employee agreements with NIC or any other department, they are not responsible for any of the problems caused because of the app.
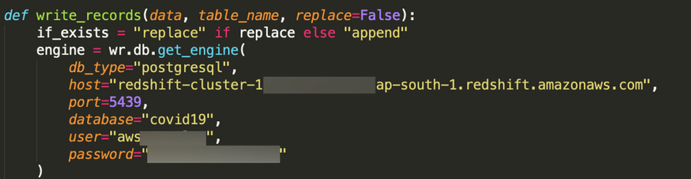
The AarogyaSetu app uses a combination of Google Cloud and Amazon Web Services for its infrastructure, ShadowMap raised concerns over using these private services for storing sensitive personal data. The ShadowMap analysis also found out the team was storing security keys to cloud infrastructure in plain-text inside the source code. In their own words, even after reporting the problem to concerned authorities, these keys were not revoked and remain active after 45 days.
One critical failure that highlights the risks associated with the Cloud Infrastructure mentioned above: The Aarogya Setu team seems to have committed their production Google Firebase Service Account Private Keys into the repository. More so, nearly 45 days since this disclosure, the keys have yet to be revoked or changed and are still active - ShadowMap
The ShadowMap team pointed the reason for these issues is lack of security audits, which are mandatory for every government IT service. They point out, even after 4 months of AarogyaSetu there has no been security audit of this complex infrastructure maintained by private players. In simple terms the team demanded transparency, third party assessment and audit trails. They summed it all by one word - Accountability.
Ministry of Electronics and Information Technology (MeITY), did not take kindly to the post by ShadowMap and issued a press release promising legal action against M/S SecurityBrigade, the company that owns ShawdowMap. The Ministry assured there was no breach of data but didn't provide any actual proof like forensic analysis to back their claims. ShawdowMap team has un-published their analysis post the threat from the ministry. MeITY also withdrew its press release after this action.
This post was adopted from the unpublished analysis by ShadowMap pointing out the problems with AarogyaSetu. You can still access their archived post.
Write a comment ...